
Photo by Towfiqu barbhuiya on Unsplash
Configuring Traefik Ingress and Clouflare in Kubernetes using Full (Strict) Encryption Mode
Introduction
If you have a Kubernetes cluster and you want to use Cloudflare this guide is for you. Cloudflare operates as a reverse proxy for the web traffic. All requests to and from the origin, will flow through Cloudflare. The benefit of this approach is that when the traffic is proxied through Cloudflare before reaching the origin server, the application gets additional security, performance, and reliability benefits. Another benefit is that we do not need to deploy Cert-Manager or Let's Encrypt. Cloudflare will handle this automatically for us.
Configuring Cloudflare
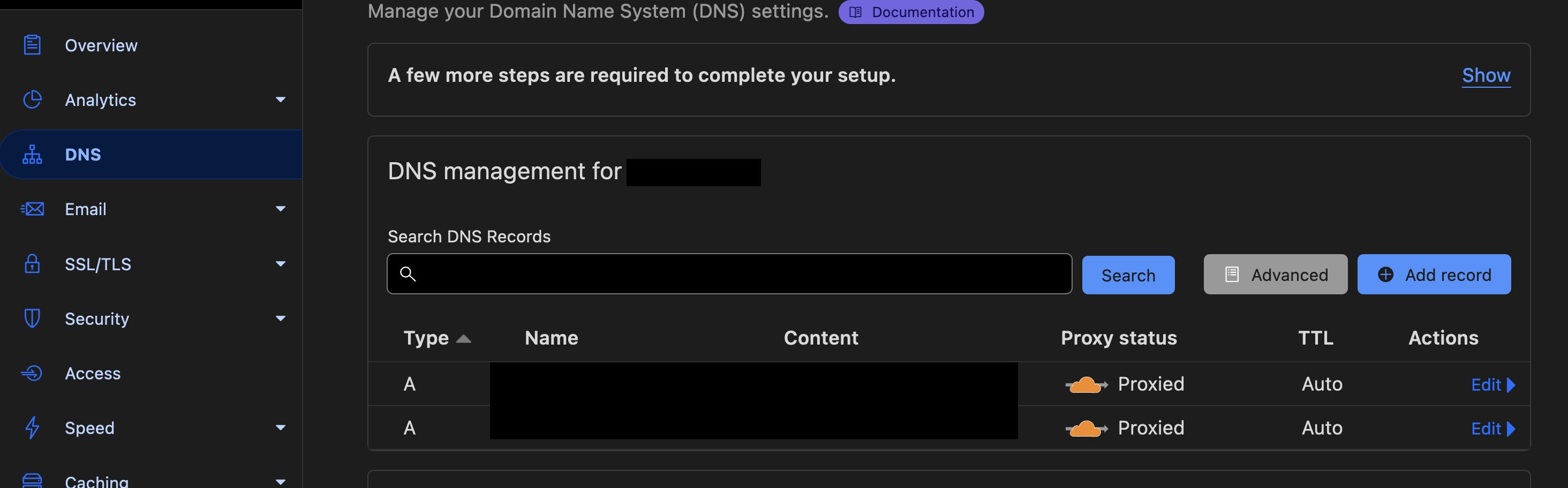
Assuming you have created a Cloudflare account and added your domain, go to your Cloudflare Dashboard and point your domain to your Load Balancer IP. If you have used the Kubernetes on Hetzner guide, point your Hetzner Load Balancer IP address that you have just created. Under DNS add two A Record. One is for the root and one is for the subdomains:
Type Name Content Proxy status TTL
A @ Your-LB-IP Proxied Auto
A * Your-LB-IP Proxied Auto
Do not forget to activate proxy:
Go to the SSL/TLS menu and activate Always Use HTTPS. You can also see that there are automatically generated Edge Certificates.
Cloudflare will automatically create a TLS certificate for connections between the end user and Cloudflare. However at this point there is no encryption between our servers and Cloudflare. This setup will work without it but I definitely recommend that you configure it.
Go to SSL/TLS from the menu and click Origin Server:
Create the certificate:
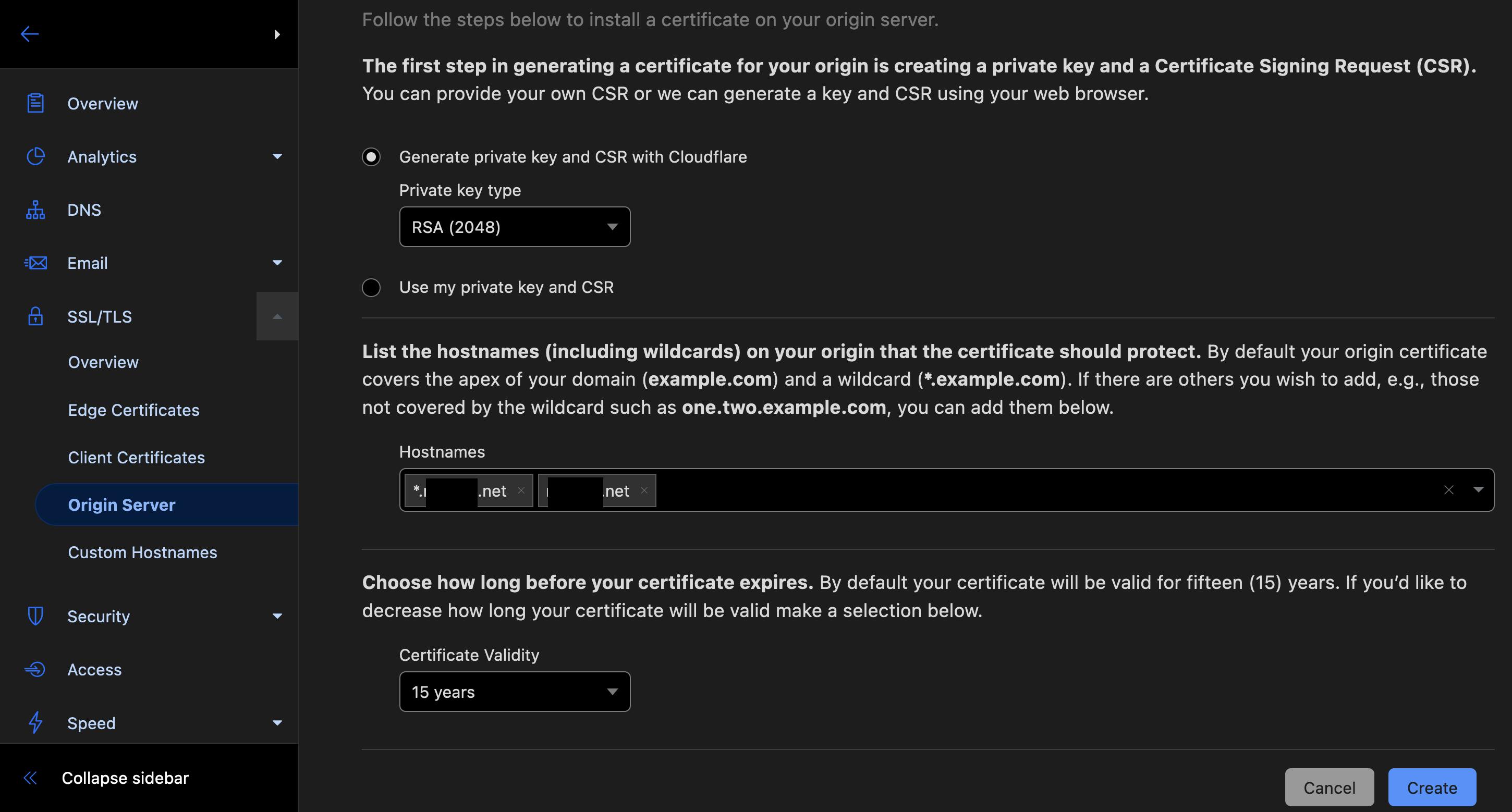
Create two files called tls.crt and tls.key
touch tls.crt
touch tls.key
and copy the certificates into these files.
Configuring Kubernetes
Afterwards create a secret inside of Kubernetes. Since this will be the default certificate for the whole cluster, you can create this secret in the kube-system namespace:
kubectl create secret generic default-cloudflare-tls -n kube-system --from-file=tls.crt=tls.crt --from-file=tls.key=tls.key
Create a Traefik store for the secret, so that you can reference it from any namespace later:
apiVersion: traefik.containo.us/v1alpha1
kind: TLSStore
metadata:
name: default-cloudflare-tls
namespace: kube-system
spec:
defaultCertificate:
secretName: default-cloudflare-tls
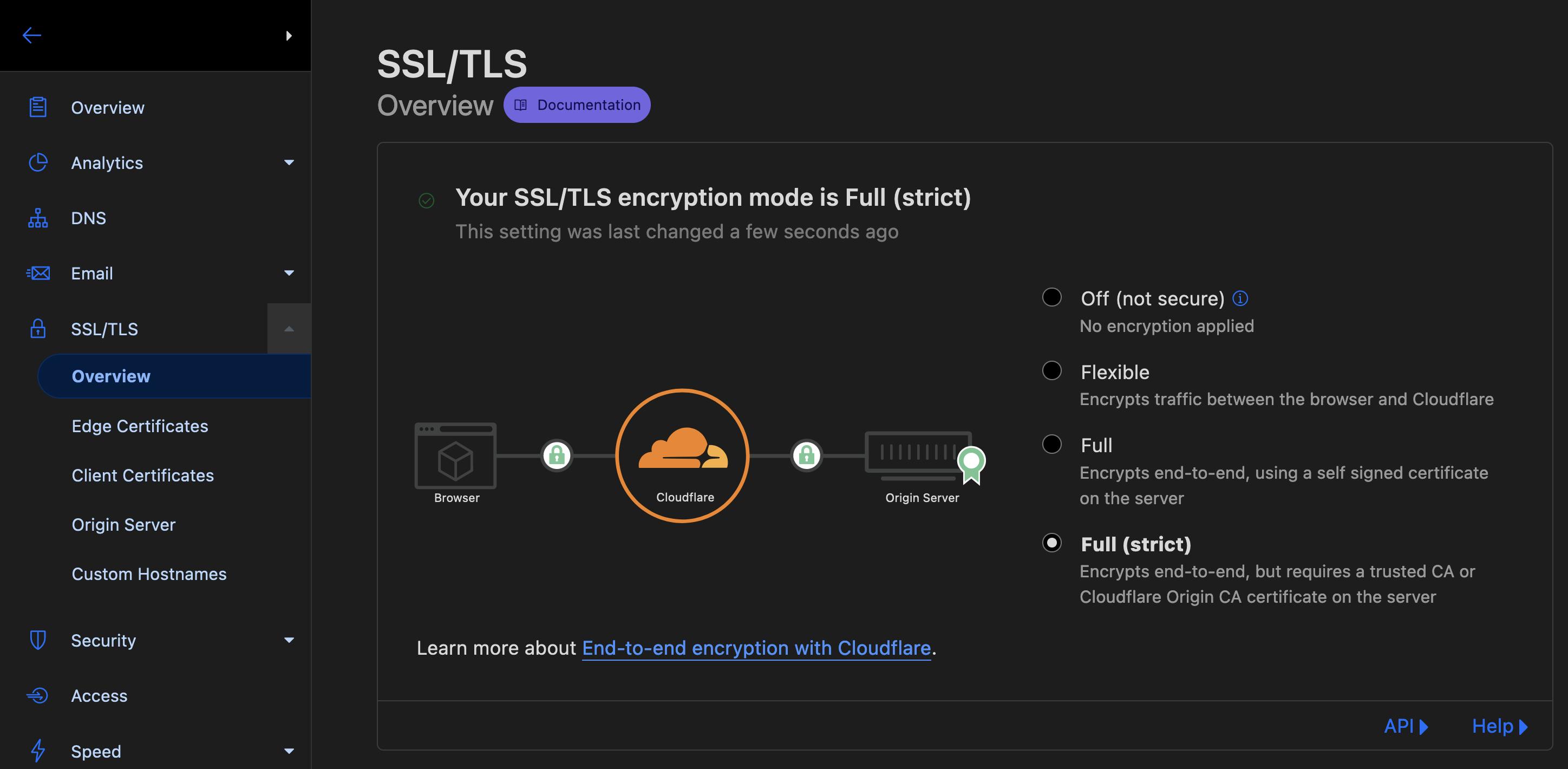
Under the SSL/TLS menu, do not forget to enable the encryption mode to Full (Strict)
Expose the Traefik Dashboard using IngressRoute
Now we will expose Traefik dashboard using an Ingressroute. Optionally you can also create a middleware for securing the Traefik Dashboard with a password. You can find more information here.
Create the ingressroute:
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: traefik-dashboard
namespace: traefik
annotations:
kubernetes.io/ingress.class: traefik-external
spec:
entryPoints:
- web
- websecure
routes:
- match: Host(`traefik.yourdomain.com`)
kind: Rule
services:
- name: api@internal
kind: TraefikService
##middlewares:
##- name: auth
tls:
store:
name: default-cloudflare-tls
We have added our Cloudflare Origin certificate in the Traefik Secret Store here:
tls:
store:
name: default-cloudflare-tls
Note: If you wish to use another Origin Certificate (for another domain etc.) you can follow the steps above, create the secret in the same namespace where your application is in, and simply add your secret like this:
tls: secretName: your-other-origin-secret
Now go to traefik.yourdomain.com, you should see a page like this:


